How To Set Encapsulation On Cisco Switch
Contents
Introduction
This document provides sample configurations on InterSwitch Link (ISL) and 802.1Q trunking between a Goad 3512-XL switch and a Cisco 2600 router; the results of each command are displayed every bit they are executed. Cisco 3600 and 4500/4700 series routers, or other members of the Cisco 2600 serial routers, with FastEthernet interfaces, and whatever Catalyst 2900XL, 3500XL, 2940, 2950 or 2970 tin exist used in the scenarios presented in this document to obtain the aforementioned results.
Trunking is a way to carry traffic from several VLANs over a point-to-betoken link betwixt the two devices. Two ways in which Ethernet trunking tin be implemented are:
-
ISL (Cisco proprietary protocol, and not supported by the 2940 or 2950 series switches)
-
802.1Q (Institute of Electric and Electronics Engineers (IEEE) standard)
Nosotros will create a trunk that will carry traffic from two VLANs (VLAN1 and VLAN2) beyond a single link between a Catalyst 3500 and a Cisco 2600 router.
We are using the Cisco 2600 router to do the Inter-VLAN routing between VLAN1 and VLAN2. Goad 2900XL/3500XL/2940/2950/2970 series switches are Layer two (L2) switches, and are not capable of routing or communicating betwixt the VLANs. For further details on Inter-VLAN routing, refer to the Routing Betwixt Virtual LANs Overview chapter of the Cisco IOS® Switching Services Configuration Guide, Release 12.ane.
To create the examples in this document, we used the following switches in a lab environment with cleared configurations:
-
Catalyst 3512XL switch running Cisco IOS 12.0(5.10)XU
-
Cisco 2621 router running Cisco IOS 12.1(three)T
-
Cisco 2621 router running Cisco IOS 12.one(ane)T
The configurations in this document were implemented in an isolated lab environment. Ensure that you understand the potential bear on of any configuration or command on your network before using it. The configurations on all devices were cleared with the write erase control to ensure that they take a default configuration.
Before You lot Brainstorm
Conventions
For more than information on document conventions, refer to the Cisco Technical Tips Conventions.
Prerequisites
At that place are no specific prerequisites for this certificate.
Components Used
This document is non restricted to specific software and hardware versions.
Of import Notes
For Goad 2900XL/3500XL/2940/2950/2970 Switches:
Catalyst 2940 and 2950 serial switches only support 802.1q trunking, and do not support ISL trunking.
On a 4 MB DRAM Goad 2900XL switch, trunking is but supported with the following trunking-capable modules:
-
WS-X2914-Forty-Five: four-port ten/100 ISL/802.1Q switch module
-
WS-X2922-XL-V: two-port 100BaseFX ISL/802.1Q switch module
-
WS-X2924-Xl-V: 4-port 100BaseFX ISL/802.1Q switch module
-
WS-X2931-Forty: 1000BaseX uplink for Catalyst 2900 XL
-
WS-X2932-XL: 1000BaseT uplink for Goad 2900 XL
Refer to Table 1 below for a electric current list of switch models that back up trunking:
Tabular array 1
| Switch Models | Minimum Release Required for ISL Trunking | Minimum Release Required for IEEE 802.1Q Trunking | Electric current Release Required for Trunking (ISL/802.1Q) |
|---|---|---|---|
| WS-C2916M-Xl (4-One thousand thousand Switch) | 11.2(8)SA4 (Enterprise Edition) | 11.two(viii)SA5 (Enterprise Edition) | xi.ii(8.6)SA6 (Original Edition) |
| C2912-XL | 11.two(8)SA4 (Enterprise Edition) | 11.2(8)SA5 (Enterprise Edition) | 12.0(5)WC(1) or later |
| C2924-Forty | 11.ii(8)SA4 (Enterprise Edition) | 11.2(8)SA5 (Enterprise Edition) | 12.0(5)WC(i) or after |
| WS-C2924C-Twoscore | eleven.2(eight)SA4 (Enterprise Edition) | 11.2(viii)SA5 (Enterprise Edition) | 12.0(5)WC(1) or later |
| WS-C2924M-Twoscore | 11.2(eight)SA4 (Enterprise Edition) | 11.2(8)SA5 (Enterprise Edition) | 12.0(5)WC(1) or after |
| WS-C2912MF-40 | 11.2(eight)SA4 (Enterprise Edition) | 11.2(eight)SA5 (Enterprise Edition) | 12.0(5)WC(1) or later |
| WS-C2924M-XL-DC | 12.0(5)XU | 12.0(5)XU | 12.0(5)WC(one) or later |
| WS-C3508G-Xl | 11.2(viii)SA4 (Enterprise Edition) | 11.2(8)SA5 (Enterprise Edition) | 12.0(5)WC(ane) or later on |
| WS-C3512-XL | xi.2(8)SA4 (Enterprise Edition) | 11.2(8)SA5 (Original Edition) | 12.0(5)WC(1) or later |
| WS-C3524-Xl | 11.two(eight)SA4 (Enterprise Edition) | xi.ii(8)SA5 (Enterprise Edition) | 12.0(five)WC(1) or later |
| WS-C3548-Twoscore | 12.0(5)XP (Enterprise Edition) | 12.0(5)XP (Enterprise Edition) | 12.0(5)WC(i) or later on |
| WS-C3524-PWR-XL | 12.0(5)XU | 12.0(5)XU | 12.0(5)WC(1) or afterwards |
| WS-C2940-8TF | ISL Not Supported | 12.1(13)AY | 12.ane(13)AY or later for 802.1Q. ISL is not supported. |
| WS-C2940-8TT | ISL Not Supported | 12.1(thirteen)AY | 12.1(13)AY or later for 802.1Q. ISL is non supported. |
| WS-C2950-12 | ISL Not Supported | 12.0(5)WC(1) | 12.0(5)WC(1) or later for 802.1Q. ISL is not supported. |
| WS-C2950-24 | ISL Not Supported | 12.0(5)WC(1) | 12.0(v)WC(1) or afterwards for 802.1Q. ISL is not supported. |
| WS-C2950C-24 | ISL Not Supported | 12.0(5)WC(1) | 12.0(5)WC(ane) or later for 802.1Q. ISL is not supported. |
| WS-C2950T-24 | ISL Not Supported | 12.0(5)WC(1) | 12.0(v)WC(1) or afterward for 802.1Q. ISL is non supported. |
| WS-C2950G-12-EI | ISL Non Supported | 12.0(5)WC(1) | 12.0(5)WC(ane) or later for 802.1Q. ISL is not supported. |
| WS-C2950G-24-EI | ISL Not Supported | 12.0(v)WC(ane) | 12.0(5)WC(1) or later for 802.1Q. ISL is non supported. |
| WS-C2950G-48-EI | ISL Non Supported | 12.0(v)WC(1) | 12.0(v)WC(one) or later for 802.1Q. ISL is non supported. |
| WS-C2950SX-24 | ISL Not Supported | 12.0(5)WC(1) | 12.0(5)WC(one) or subsequently for 802.1Q. ISL is not supported. |
| WS-C2950-24-EI-DC | ISL Non Supported | 12.0(5)WC(1) | 12.0(five)WC(1) or subsequently for 802.1Q. ISL is not supported. |
| WS-C2955T-12 | ISL Not Supported | 12.1(13)EA1 | 12.1(13)EA1 or later for 802.1Q. ISL is not supported. |
| WS-C2955S-12 | ISL Not Supported | 12.1(thirteen)EA1 | 12.1(xiii)EA1 or later for 802.1Q. ISL is not supported. |
| WS-C2955C-12 | ISL Non Supported | 12.1(13)EA1 | 12.i(13)EA1 or later for 802.1Q. ISL is not supported. |
| WS-C2970G-24T | 12.1(eleven)AX | 12.one(11)AX | 12.1(xi)AX or later |
| WS-C2970G-24TS | 12.one(xiv)EA1 | 12.ane(xiv)EA1 | 12.1(14)EA1 or later |
Note:In the above table, only WS-C2916M-XL is a four MB DRAM switch. All the other switches listed are 8 MB DRAM switches. To determine whether your switch has 4 MB or 8 MB of DRAM, enter the user-level show version control. For more than data, run into the How to Decide the Amount of Switch Memory Using the Command Line Interface department of Upgrading Software in Goad 2900-XL/3500-Forty Switches Using the Command Line Interface.
Note:In Catalyst 2900XL/3500XL/2940/2950/2970 switches, a VLAN interface, for example, int vlan ane, int vlan 2, int vlan x, can be created for each and every VLAN that is configured on the switch. Nevertheless, only one VLAN tin be used at a time every bit a management VLAN. The IP address is assigned to the VLAN interface of the management VLAN only. If the IP accost is assigned to some other VLAN interface whose VLAN is non used equally direction VLAN, that interface will non come. It is preferred to create the VLAN interface only for the management VLAN.
For Cisco 2600 Routers:
For 802.1Q trunking, one VLAN is not tagged. This VLAN is called native VLAN. The native VLAN is used for untagged traffic when the port is in 802.1Q trunking way. While configuring 802.1Q trunking, it is very of import to keep in heed that the native VLAN must be configured the same on each side of the trunk link. It is a mutual error non to match the native VLANs while configuring 802.1Q trunking between the router and the switch. For details on native VLANs, refer to the IEEE 802.1Q section of Bridging Between IEEE 802.1Q VLANs, in New Features in Release 12.one(3)T.
In this sample configuration, the native VLAN is VLAN1, by default, on both the Cisco 2621 router and the Catalyst 3512XL switch. Depending on your network needs, you may have to use a native VLAN other than the default VLAN, VLAN1. Commands have been mentioned in the Configurations department of this certificate on how to change the native VLAN on the Cisco 2600 router and Catalyst 3500XL switch.
Sample configurations presented in this document tin can exist used on Cisco 2600/3600/4500/4700 series routers with Fast Ethernet interfaces or Fast Ethernet network modules. Besides, make sure that you are using the Cisco IOS version that supports ISL/802.1Q VLAN trunking. For a complete list of Cisco 2600/3600/4500/4700 routers that back up ISL/802.1Q VLAN trunking and the supported Cisco IOS versions, refer to Tabular array ii below.
Tabular array two
| Router Models | Minimum Release Required for ISL Trunking | Minimum Release Required for IEEE 802.1Q Trunking | Minimum Required Feature Set (ISL/802.1Q) |
|---|---|---|---|
| Cisco 2620 | 11.3(3a)T | 12.0(1)T | IP PLUS / IP PLUS |
| Cisco 2621 | 11.iii(3a)T | 12.0(1)T | IP PLUS / IP PLUS |
| Cisco 2620 | 12.1(3a)T | 12.ane(3a)T | IP PLUS / IP PLUS |
| Cisco 2650 | 12.one(3a)T | 12.1(3a)T | IP PLUS / IP PLUS |
| Cisco 3620 | eleven.3(1)T | 12.0(1)T | IP PLUS / IP PLUS |
| Cisco 3640 | xi.3(ane)T | 12.0(one)T | IP PLUS / IP PLUS |
| Cisco 3661 | 12.0(five)T | 12.0(5)T | IP PLUS / IP PLUS |
| Cisco 3662 | 12.0(v)T | 12.0(v)T | IP PLUS / IP PLUS |
| Cisco 4500-Thou | 11.three(ane)T | 12.0(1)T | IP PLUS / IP PLUS |
| Cisco 4700-M | 11.3(one)T | 12.0(one)T | IP PLUS / IP PLUS |
Note:Table 2 only lists the minimum or current maintenance/main releases that support this sample configuration. Router models with certain network modules may have unlike minimum Cisco IOS versions. For a complete list of minimum supported software for any router family, utilize the Software Advisor (registered customers only) .
Note:The minimum supported release may not necessarily be the recommended release. To determine the best maintenance release for your Cisco production, search for bugs listed by product component in the Issues Toolkit (registered customers only) .
Annotation:Table ii lists the minimum characteristic set required to do IP Inter-VLAN routing and trunking to support this sample configuration. For a complete listing of other feature sets supported in unlike Cisco IOS versions and on different platforms, utilize the Download Software area.
Configure
In this section, you are presented with the information to configure the features described in this document.
Notation:To find boosted information on the commands used in this document, utilize the Command Lookup Tool (registered customers merely) .
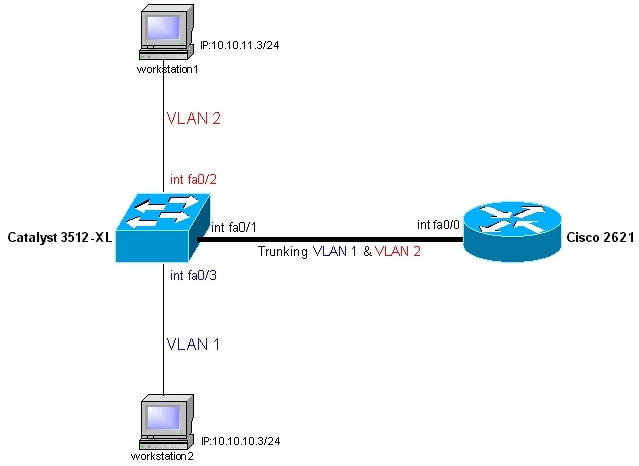
Network Diagram
This certificate uses the network setup shown in the diagram below.
Configurations
This certificate uses the configurations shown below.
Note:Router models with certain network modules may have different minimum Cisco IOS versions that support ISL trunking.
-
Catalyst 3512-Forty
-
Cisco 2600 Router
-
802.1Q Configuration on the Router for Cisco IOS Versions Earlier than 12.ane(3)T
| Catalyst 3512-XL |
|---|
| Note:The following screen captures show the commands that were entered on the 3512XL switch. Comments betwixt the commands are added in blue italics to explain sure commands and steps. !-- Prepare the privileged mode !-- and Telnet password on the switch. switch#configure terminal Enter configuration commands, ane per line. Terminate with CNTL/Z. switch(config)#hostname 3512xl 3512xl(config)#enable countersign mysecret 3512xl(config)#line vty 0 4 3512xl(config-line)#login 3512xl(config-line)#password mysecret 3512xl(config-line)#exit 3512xl(config)#no logging console 3512xl(config)#^Z !-- Fix the IP address and default gateway for VLAN1 for management purposes. 3512xl#configure concluding Enter configuration commands, one per line. Cease with CNTL/Z. 3512xl(config)#int vlan i 3512xl(config-if)#ip address 10.10.10.ii 255.255.255.0 3512xl(config-if)#leave 3512xl(config)#ip default-gateway x.10.10.ane 3512xl(config)#end !-- Set the VTP Mode. !-- In our instance, we have set the manner to exist transparent. !-- Depending on your network, set the VTP Way appropriately. !-- For details on VTP, !-- refer to !-- Creating and Maintaining VLANs on Catalyst 2900XL and 3500XL Switches. 3512xl#vlan database 3512xl(vlan)#vtp transparent Setting device to VTP TRANSPARENT mode. !-- Adding VLAN2. VLAN1 already exists past default. 3512xl(vlan)#vlan 2 VLAN 2 added: Name: VLAN0002 3512xl(vlan)#exit APPLY completed. Exiting.... !-- Enable trunking on the interface fastEthernet 0/1. 3512xl#configure final Enter configuration commands, one per line. End with CNTL/Z. 3512xl(config)#int fastEthernet 0/1 3512xl(config-if)#switchport mode trunk !-- Enter the trunking encapsulation as either isl 3512xl(config-if)#switchport trunk encapsulation isl !-- or as dot1q: 3512xl(config-if)#switchport trunk encapsulation dot1q !-- In instance of 2940/2950 series switches, none of the above 2 commands are used, !-- 2940/2950 series switches only support 802.1q encapsulation which is configured automatically, !-- when trunking is enabled on the interface by using switchport manner body command. !-- In example of dot1q, y'all demand to make sure that !-- the native VLAN matches across the link. !-- On 3512XL, by default, the native VLAN is 1. !-- Depending on your network needs, y'all may change !-- the native VLAN to be other than VLAN1, !-- but information technology is very important that y'all change the native VLAN !-- on the router accordingly. !-- Yous may modify the native VLAN, if needed, past using the following control: !-- 3512xl(config-if)#switchport trunk native vlan <vlan ID> !-- Allow all VLANs on the torso. 3512xl(config-if)#switchport trunk allowed vlan all 3512xl(config-if)#exit !-- The following ready of commands will place FastEthernet 0/2 !-- into VLAN2 and enable portfast on the interface. 3512xl(config)#int fastEthernet 0/2 3512xl(config-if)#switchport admission vlan 2 3512xl(config-if)#spanning-tree portfast 3512xl(config-if)#leave !-- FastEthernet 0/3 is already in VLAN1 by default. !-- Enable portfast on the interface. 3512xl(config)#int fastEthernet 0/3 3512xl(config-if)#spanning-tree portfast 3512xl(config-if)#^Z !-- For details on why to enable portfast, !-- refer to: !-- Using PortFast and Other Commands to Fix Workstation Startup Connectivity Delays. !-- Remember to save the configuration. 3512xl#write memory Building configuration... 3512xl# -------------------------------------------------------------------------------- 3512xl#show running-config Edifice configuration... Current configuration: ! version 12.0 no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname 3512xl ! no logging console enable password mysecret ! ! ! ! ! ip subnet-zero ! ! ! interface FastEthernet0/1 switchport mode trunk ! !-- If 802.1Q is configured, !-- y'all will instead come across the following output !-- under interface FastEthernet0/i: !-- interface FastEthernet0/1 !-- switchport trunk encapsulation dot1q !-- switchport mode trunk ! interface FastEthernet0/2 switchport admission vlan 2 spanning-tree portfast ! interface FastEthernet0/3 spanning-tree portfast ! interface FastEthernet0/4 ! interface FastEthernet0/5 ! interface FastEthernet0/six ! interface FastEthernet0/7 ! interface FastEthernet0/8 ! interface FastEthernet0/9 ! interface FastEthernet0/10 ! interface FastEthernet0/11 ! interface FastEthernet0/12 ! interface GigabitEthernet0/1 ! interface GigabitEthernet0/2 ! interface VLAN1 ip address 10.ten.x.2 255.255.255.0 no ip directed-broadcast no ip route-cache ! ip default-gateway ten.10.10.1 ! line con 0 ship input none stopbits 1 line vty 0 4 countersign mysecret login line vty five 15 login ! end |
| 2600 Router |
|---|
| Note:The following screen captures testify the commands that were entered on the Cisco 2600 router. Comments between the commands are added in blue italics to explain certain commands and steps. !-- Set the privileged manner !-- and Telnet countersign on the router. Router#configure terminal Enter configuration commands, one per line. Cease with CNTL/Z. Router(config)#hostname c2600 c2600(config)#enable password mysecret c2600(config)#line vty 0 4 c2600(config-line)#login c2600(config-line)#password mysecret c2600(config-line)#exit c2600(config)#no logging console c2600(config)#^Z c2600#configure terminal Enter configuration commands, ane per line. End with CNTL/Z. !-- Select FastEthernet 0/0 for the body configuration. !-- No L2 or Layer 3 (L3) configuration is done here. c2600(config)#int fastEthernet 0/0 c2600(config-if)#no shut c2600(config-if)#exit !-- Enable trunking on the sub-interface FastEthernet 0/0.i. !-- Note that bodily trunks are configured on the sub-interfaces. c2600(config)#int fastEthernet 0/0.1 !-- Enter the trunking encapsulation as either isl c2600(config-subif)#encapsulation isl 1 !-- or every bit dot1q: !-- In example of dot1q, you need to make sure that !-- the native VLAN matches across the link. !-- On 3512XL, by default, the native VLAN is ane. !-- On the router, configure VLAN1 equally the native VLAN. c2600(config-subif)#encapsulation dot1Q 1 ? native Make this is native vlan <cr> c2600(config-subif)#encapsulation dot1Q 1 native !-- On the switch, if you have a native VLAN other than VLAN1, !-- on the router, configure the aforementioned VLAN to be the native VLAN, !-- by using the above control. Note:The encapsulation dot1Q i native command was added in Cisco IOS version 12.1(3)T. If yous are using an earlier version of Cisco IOS, refer to the 802.1Q configuration for Cisco IOS Versions Earlier than 12.1(three)T section of this document to configure 802.1Q trunking on the router. !-- Configure L3 information on the sub-interface 0/0.one. c2600(config-subif)#ip address 10.10.10.i 255.255.255.0 c2600(config-subif)#exit !-- Enable trunking on the sub-interface FastEthernet 0/0.two. !-- Annotation that actual trunks are configured on the sub-interfaces. c2600(config)#int fastEthernet 0/0.2 !-- Enter the trunking encapsulation as either isl c2600(config-subif)#encapsulation isl ii !-- or every bit dot1q: c2600(config-subif)#encapsulation dot1Q ii !-- Configure L3 data on the sub-interface 0/0.ii. c2600(config-subif)#ip accost 10.10.eleven.1 255.255.255.0 c2600(config-subif)#exit c2600(config)#^Z !-- Remember to relieve the configuration. c2600#write memory Edifice configuration... [OK] c2600# Note:In order to brand this setup piece of work, and to successfully ping between workstation1 and workstation2, you need to make sure that the default gateways on the workstations are setup properly. For workstation1, the default gateway should be 10.x.xi.1 and for workstation2, the default gateway should be 10.10.10.ane. For details on how to set the default gateways on the workstations, refer to their respective sections in this document. Notation:The following paragraph is just applicable, if you have configured 802.1Q trunking between the router and the switch. Note:If you lot have followed the configuration steps listed in the in a higher place sections, and are still not able to ping beyond the VLANs (betwixt workstation1 and workstation2), and so there is a possibility that yous have come beyond Caveat CSCds42715, in which the 802.1Q native VLAN keyword does not role properly when fast switching is enabled. The bug prepare was integrated in the following code versions: 12.2(0.5), 12.2(0.five)T, 12.i(v)DC, 12.i(v)YB, 12.2(0.18)Southward, 12.i(5)YD02, 12.2(2)B, 12.2(fifteen)ZN. You lot can cheque the condition and a cursory description of the bug by using the Bug Toolkit (registered customers but) and entering the bug ID CSCds42715. -------------------------------------------------------------------------------- c2600#show running-config Building configuration... Electric current configuration: ! version 12.1 service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname c2600 ! no logging console enable password mysecret ! ! ! ! ! ip subnet-zippo ! ! ! ! ! ! ! ! ! ! interface FastEthernet0/0 no ip address duplex motorcar speed auto ! interface FastEthernet0/0.1 encapsulation isl 1 ip address x.ten.10.ane 255.255.255.0 no ip redirects ! !-- If 802.1Q is configured, !-- you lot will instead run into the post-obit output !-- nether interface FastEthernet0/0.1: !-- interface FastEthernet0/0.1 !-- encapsulation dot1Q 1 native !-- ip address x.ten.10.ane 255.255.255.0 ! ! interface FastEthernet0/0.2 encapsulation isl 2 ip accost 10.10.11.1 255.255.255.0 no ip redirects ! !-- If 802.1Q is configured, !-- you volition instead run into the post-obit output !-- under interface FastEthernet0/0.two: !-- interface FastEthernet0/0.2 !-- encapsulation dot1Q 2 !-- ip address 10.ten.eleven.1 255.255.255.0 ! interface FastEthernet0/i no ip address shutdown duplex motorcar speed car ! ip classless no ip http server ! ! ! line con 0 transport input none line aux 0 line vty 0 four password mysecret login ! no scheduler allocate end |
| 802.1Q Configuration on the Router for Cisco IOS Versions Before than 12.i(3)T |
|---|
As described earlier in this document, while configuring 802.1Q trunking it is very important to lucifer the native VLAN across the link. In the Cisco IOS software versions earlier than 12.1(three)T, yous cannot define the native VLAN explicitly, as the encapsulation dot1Q i native command under the sub-interface is not available. In the earlier Cisco IOS versions, it is important to configure the native VLAN-Interface not every bit a sub-interface, which is in our case VLAN1. If configured incorrect, the router would expect a tag dot1q frame on VLAN1 and the switch is not expecting a tag on VLAN1. As a result, no traffic will pass between VLAN1 on the switch and the router. In these situations always put the configuration for the native VLAN under the chief interface and on the trunk create subinterface for all other VLANS. In the current lab setup, apply the post-obit steps to configure the Cisco 2600 router: !-- Set the privileged mode !-- and Telnet countersign on the router. Router#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Router(config)#hostname c2600 c2600(config)#enable password mysecret c2600(config)#line vty 0 4 c2600(config-line)#login; c2600(config-line)#password mysecret c2600(config-line)#get out c2600(config)#no logging console c2600(config)#^Z c2600#configure last Enter configuration commands, one per line. End with CNTL/Z. !-- Select FastEthernet 0/0 for the trunk configuration. c2600(config)#int fastEthernet 0/0 c2600(config-if)#no shut !-- Note that the IP address for VLAN1 is configured on the main interface, !-- and no encapsulation for VLAN1 will exist washed under the sub-interface. c2600(config-if)#ip address 10.10.10.1 255.255.255.0 c2600(config-if)#exit !-- Configure dot1q encapsulation for VLAN 2 !-- on sub-interface fastEthernet 0/0.2. c2600(config)#int fastEthernet 0/0.2 c2600(config-subif)#encapsulation dot1Q ii c2600(config-subif)# !-- Configuring L3 information on the sub-interface 0/0.ii. c2600(config-subif)#ip address ten.10.11.1 255.255.255.0 c2600(config-subif)#exit c2600(config)#^Z !-- Think to save the configuration. c2600#write memory Building configuration... [OK] c2600# Note:In society to make this setup work and to successfully ping between workstation1 and workstation2, yous need to make certain that the default gateways on the workstations are setup properly. For workstation1, the default gateway should be 10.10.11.1, and for workstation2, the default gateway should be 10.10.10.one. For details on how to set up the default gateways on the workstations, refer to thei respective sections in this document. c2600#show running-config Building configuration... Current configuration: ! version 12.ane service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname c2600 ! no logging console enable countersign mysecret ! ! ! ! ! memory-size iomem 7 ip subnet-goose egg ! ! ! ! ! ! ! interface FastEthernet0/0 ip address 10.10.10.1 255.255.255.0 duplex motorcar speed auto ! interface FastEthernet0/0.ii encapsulation dot1Q two ip address 10.ten.11.1 255.255.255.0 ! interface FastEthernet0/1 no ip address shutdown duplex automobile speed car ! ip classless no ip http server ! ! line con 0 transport input none line aux 0 line vty 0 iv password mysecret login ! no scheduler classify end c2600# |
debug and show Commands
This department provides information you can use to confirm your configuration is working properly.
Certain prove commands are supported by the Output Interpreter Tool (registered customers only) , which allows you to view an analysis of prove command output.
On the Catalyst 2900XL/3500XL/2940/2950/2970 switch, use the following commands:
-
show int {FastEthernet | GigabitEthernet} <module/port> switchport
-
evidence vlan
-
show vtp status
On the Cisco 2600 router, use the following commands:
-
show vlan
-
show interface
Sample show Command Output
Catalyst 3500XL Switch
prove int {FastEthernet | GigabitEthernet} <module/port> switchport
This command is used to cheque the administrative and operational status of the port. It is also used to make sure that the native VLAN matches on both sides of the trunk. The native VLAN is used for untagged traffic when the port is in 802.1Q trunking style. Refer to Creating and Maintaining VLANs on Catalyst 2900XL and 3500XL Switches for details on native VLANs.
3512xl#show int fastEthernet 0/1 switchport Proper name: Fa0/one Switchport: Enabled Administrative mode: trunk Operational Mode: trunk Administrative Trunking Encapsulation: isl Operational Trunking Encapsulation: isl Negotiation of Trunking: Disabled Access Mode VLAN: 0 ((Inactive)) Trunking Native Mode VLAN: one (default) Trunking VLANs Enabled: ALL Trunking VLANs Active: ane,2 Pruning VLANs Enabled: two-1001 Priority for untagged frames: 0 Override vlan tag priority: FALSE Voice VLAN: none Apparatus trust: none
Note:For 802.1Q trunking, the output of the to a higher place control changes every bit follows:
3512xl#bear witness int fastEthernet 0/1 switchport Name: Fa0/1 Switchport: Enabled Authoritative mode: body Operational Mode: trunk Authoritative Trunking Encapsulation: dot1q Operational Trunking Encapsulation: dot1q Negotiation of Trunking: Disabled Admission Mode VLAN: 0 ((Inactive)) Trunking Native Way VLAN: 1 (default) Trunking VLANs Enabled: ALL Trunking VLANs Agile: 1,2 Pruning VLANs Enabled: 2-1001 Priority for untagged frames: 0 Override vlan tag priority: FALSE Vocalization VLAN: none
testify vlan
This command is used to verify that the interfaces (ports) belong to the correct VLAN. In our example, but interface Fa0/two belongs to VLAN2. The rest are members of VLAN1.
3512xl#evidence vlan VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- i default agile Fa0/3, Fa0/4, Fa0/5, Fa0/vi, Fa0/7, Fa0/8, Fa0/9, Fa0/x, Fa0/11, Fa0/12, Gi0/i, Gi0/2 2 VLAN0002 active Fa0/2 1002 fddi-default agile 1003 token-ring-default agile 1004 fddinet-default active 1005 trnet-default active ...(output suppressed)
show vtp status
This control is used to check the VLAN trunking protocol (VTP) configuration on the switch. In our example, we have used transparent mode. The correct VTP mode depends on the topology of your network. For details on VTP, refer to Creating and Maintaining VLANs on Catalyst 2900XL and 3500XL Switches.
3512xl#evidence vtp status VTP Version : 2 Configuration Revision : 0 Maximum VLANs supported locally : 254 Number of existing VLANs : 6 VTP Operating Way : Transparent VTP Domain Proper noun : VTP Pruning Mode : Disabled VTP V2 Style : Disabled VTP Traps Generation : Disabled MD5 digest : 0xC3 0x71 0xF9 0x77 0x2B 0xAC 0x5C 0x97 Configuration concluding modified by 0.0.0.0 at 0-0-00 00:00:00
Cisco 2600 Router
show vlan
This control tells you what L2 or L3 information is configured for each VLAN.
c2600#testify vlan Virtual LAN ID: 1 (Inter Switch Link Encapsulation) vLAN Trunk Interface: FastEthernet0/0.ane Protocols Configured: Accost: Received: Transmitted: IP 10.10.10.one xl 38 Virtual LAN ID: two (Inter Switch Link Encapsulation) vLAN Torso Interface: FastEthernet0/0.2 Protocols Configured: Address: Received: Transmitted: IP 10.10.11.1 9 9
Note:For 802.1Q trunking, the output of the to a higher place command changes as follows:
c2600#bear witness vlan Virtual LAN ID: 1 (IEEE 802.1Q Encapsulation) vLAN Trunk Interface: FastEthernet0/0.1 This is configured equally native Vlan for the following interface(due south): FastEthernet0/0 Protocols Configured: Address: Received: Transmitted: IP x.10.10.ane 0 ii Virtual LAN ID: 2 (IEEE 802.1Q Encapsulation) vLAN Torso Interface: FastEthernet0/0.ii Protocols Configured: Address: Received: Transmitted: IP ten.10.eleven.i 42 19
Note:For 802.1Q trunking, with Cisco IOS versions before and so 12.one(3)T, the output of the command changes as follows:
c2600#show vlan Virtual LAN ID: 2 (IEEE 802.1Q Encapsulation) vLAN Trunk Interface: FastEthernet0/0.ii Protocols Configured: Address: Received: Transmitted: IP ten.10.11.1 6 iv
Note:No IEEE 802.1Q encapsulation is displayed for VLAN1 on whatsoever of the sub-interfaces.
show interface
This control is used to bank check the administrative and operational condition of the interface.
c2600#show interfaces fastEthernet 0/0 FastEthernet0/0 is upwards, line protocol is up Hardware is AmdFE, address is 0003.e36f.41e0 (bia 0003.e36f.41e0) MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec, reliability 255/255, txload one/255, rxload 1/255 Encapsulation ARPA, loopback not set Keepalive set (10 sec) Full-duplex, 100Mb/s, 100BaseTX/FX ARP type: ARPA, ARP Timeout 04:00:00 Last input 00:00:00, output 00:00:07, output hang never Last clearing of "prove interface" counters never Queueing strategy: fifo Output queue 0/40, 0 drops; input queue 0/75, 0 drops 5 infinitesimal input rate 0 bits/sec, one packets/sec five minute output rate 0 bits/sec, 0 packets/sec 217 packets input, 12884 bytes Received 217 broadcasts, 0 runts, 0 giants, 0 throttles 0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored 0 watchdog 0 input packets with dribble condition detected 45 packets output, 6211 bytes, 0 underruns(0/0/0) 0 output errors, 0 collisions, 4 interface resets 0 babbles, 0 late standoff, 0 deferred 0 lost carrier, 0 no carrier 0 output buffer failures, 0 output buffers swapped out c2600#evidence interfaces fastEthernet 0/0.1 FastEthernet0/0.ane is up, line protocol is upwardly Hardware is AmdFE, accost is 0003.e36f.41e0 (bia 0003.e36f.41e0) Cyberspace address is x.10.10.ane/24 MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec, reliability 255/255, txload i/255, rxload 1/255 Encapsulation ISL Virtual LAN, Colour 1. ARP type: ARPA, ARP Timeout 04:00:00 c2600#show interfaces fastEthernet 0/0.2 FastEthernet0/0.two is upwardly, line protocol is upwardly Hardware is AmdFE, address is 0003.e36f.41e0 (bia 0003.e36f.41e0) Internet address is 10.10.11.1/24 MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation ISL Virtual LAN, Colour 2. ARP type: ARPA, ARP Timeout 04:00:00
Note:For 802.1Q trunking, the output of the above control changes equally follows:
c2600#bear witness interfaces fastEthernet 0/0.one FastEthernet0/0.1 is up, line protocol is up Hardware is AmdFE, accost is 0003.e36f.41e0 (bia 0003.e36f.41e0) Internet address is ten.10.ten.1/24 MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec, reliability 255/255, txload ane/255, rxload 1/255 Encapsulation 802.1Q Virtual LAN, Vlan ID ane. ARP type: ARPA, ARP Timeout 04:00:00 c2600#show interfaces fastEthernet 0/0.ii FastEthernet0/0.2 is upwardly, line protocol is upward Hardware is AmdFE, address is 0003.e36f.41e0 (bia 0003.e36f.41e0) Internet address is 10.10.11.1/24 MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec, reliability 255/255, txload 1/255, rxload i/255 Encapsulation 802.1Q Virtual LAN, Vlan ID 2. ARP blazon: ARPA, ARP Timeout 04:00:00
Related Data
- Configuring 802.1q Trunking Betwixt a Catalyst 3550/3750 and Catalyst Switches
- Creating and Maintaining VLANs on Goad 2900XL and 3500XL Switches
- Creating and Maintaining VLANs on Catalyst 2950 Switches
- Using PortFast and Other Commands to Fix Workstation Startup Connectivity Delays
- Catalyst 2900XL/3500XL, Cisco IOS Desktop Switching Control Reference
- Catalyst 2940 Switch Control Reference
- Catalyst 2950 and Goad 2955 Switch Control Reference
- Catalyst 2970 Switch Command Reference
- XC: Cisco IOS Switching Services Configuration Guide
- XR: Cisco IOS Switching Services Control Reference
- Technical Support - Cisco Systems
Source: https://www.cisco.com/c/en/us/support/docs/lan-switching/inter-vlan-routing/14976-50.html

0 Response to "How To Set Encapsulation On Cisco Switch"
Post a Comment